"WP Security Helper" - The Stealth Backdoor Infecting 3,500+ WordPress Sites

Our security research team has identified a massive campaign targeting WordPress websites through a fake plugin titled "WP Security Helper." To date, we have confirmed infections on over 3,500 websites.
Unlike typical malware that causes visible damage, this plugin is designed for maximum stealth. It uses a "Gaslighting" technique—manipulating the WordPress core to hide its own existence and the existence of any other attacker-controlled accounts.

The Attack Vector: Admin Hijacking
The campaign relies on compromised administrator credentials, likely obtained via credential stuffing, stolen cookies or large-scale phishing. Once attackers gain access to wp-admin, they upload the "WP Security Helper" plugin. We have tracked these uploads back to a specific set of malicious IP addresses (listed in the IOCs below).
How the Malware Works: Technical Analysis
The code uses PHP goto statements and hex/octal string obfuscation (e.g., \165\163\x65\x72\x73\x2e\160\150\160 translates to users.php) to bypass basic scanners. Here is what the code actually does once activated:
1. Hiding Attacker Accounts (The User Ghosting)
The plugin hooks into pre_get_users and get_users. It intercepts every request the WordPress admin makes to see the "Users" list.
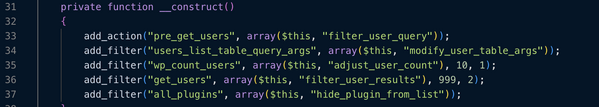
- The Manipulation: It forcibly filters the user list to only show the currently logged-in user.
- The Result: If an attacker creates five "shadow" admin accounts, a legitimate admin will never see them. The legitimate admin looks at the user list, sees only their own name, and assumes they are the only person with access.
2. Faking the User Count

To further the deception, the plugin hooks into wp_count_users. Even if there are 10 hidden admin accounts in the database, the plugin overwrites the total count and displays "1" on the dashboard. This prevents administrators from noticing a discrepancy between the listed users and the "Total" count.
3. Self-Invisibility

The plugin includes a function called hide_plugin_from_list. It removes itself from the all_plugins filter. Unless you pass a specific secret parameter, the "WP Security Helper" will not appear in the WordPress Plugins menu. It is essentially a "ghost" plugin.
Recommendations
- Force Logout, Password Reset & Salt Keys rotation: Immediately terminate all sessions and reset all administrator passwords and rotate all the KEYS listed in the
wp-config.phpof the site. - Manual File Deletion: Because the plugin hides itself from the GUI, you must delete the folder
/wp-content/plugins/wp-security-helper/via FTP/sFTP/SSH or your hosting File Manager. - Audit the Database: Check the
wp_userstable for any accounts you did not personally create.
Indicators of Compromise (IOCs)
If you suspect your site is part of this 3,500+ site botnet, check for the following indicators.
File System & Database
- Plugin Directory:
/wp-content/plugins/wp-security-helper/ - Main File:
wp-security-helper.php - SHA256 Hashes:
0a26e477951896659dbc5b0b18929995303a9ab4e071288b40691e0b366b96a1adec373f181b9b8edbc413346b98067ab1aa5704af97bb9d9d65ed387ecd2529
Malicious Source IPs
These IPs have been identified as the primary sources of the wp-admin logins and plugin deployments:
216.229.112.25216.26.255.231216.26.255.180216.26.249.120213.232.122.23209.50.186.38194.99.27.172185.202.108.240185.202.108.233178.20.31.191170.168.97.108
Note: The specific IP addresses & domains provided above are the ones observed during the investigation. Specific, actionable IPs & domains should be validated with your threat intelligence feeds.

